Why NDR is crucial to detect zero-day exploits
Understanding Zero-Day Exploits
Within the realm of cybersecurity, zero-day exploits pose a unique challenge to consumers and vendors alike; how do you identify and mitigate the risks of an unknown vulnerability in real time? These threats exploit vulnerabilities in software, hardware, or protocols that are not yet known to the vendor or the broader cybersecurity community. Known vulnerabilities can be patched or mitigated once identified, while zero-day vulnerabilities leave organizations vulnerable to exploitation until effective countermeasures are developed and deployed.
The term “zero-day” refers to the fact that organizations have zero days of prior awareness or preparation for these threats before they are actively exploited by malicious actors. Here’s how damaging they can be:
- This lack of prior knowledge leaves organizations susceptible to significant risks, including unauthorized access to systems, exfiltration of sensitive data, disruption of critical operations, and more.
- Further, zero-day exploits often target widely used software applications, operating systems, or network protocols, amplifying their potential impact across diverse industries and sectors.
- Malicious actors have even compromised supply chains, infiltrating trusted vendor networks or tampering with software repositories to introduce malicious code or backdoors into otherwise legitimate software packages.
By compromising the integrity of vendor-certified software, attackers can exploit unsuspecting consumers who trust the authenticity and security of these products by injecting a zero-day threat further up the supply chain (more on supply chain attacks here).
As a result, zero-day exploits pose a pervasive and ever-evolving challenge, necessitating continuous vigilance, proactive defense strategies, and rapid response capabilities. Understanding the nature of zero-day threats, their potential consequences, and the limitations of traditional security measures is essential for organizations seeking to mitigate the risks posed by these complex vulnerabilities.
In the subsequent sections, we will explore the inherent limitations of traditional security measures in combatting zero-day exploits and examine the crucial role of Network Detection and Response (NDR) solutions in uncovering blind spots and bolstering organizational defenses.
The Limitations of Traditional Security Measures
Traditional security measures, while effective against known threats, often fall short when confronted with the complexities of zero-day attacks. Signature-based antivirus software, for instance, relies on a database of known malware signatures to identify and block malicious files.
However, since a zero-day threat lacks an existing signature, it can often evade detection by these systems. Similarly, perimeter-based firewalls inspect network traffic based on predefined rules, which may overlook sophisticated zero-day exploits that exploit protocol-level vulnerabilities or masquerade as legitimate traffic.
These limitations highlight the inherent challenge of relying solely on static, rule-based defenses in an environment where threats are dynamic and rapidly evolving. Traditional security measures are reactive by nature, relying on the detection of known patterns or signatures to identify and respond to threats. However, zero-day exploits operate outside the realm of known patterns, making them particularly elusive and difficult to detect using traditional methods.
As a result, organizations relying solely on traditional security measures find themselves vulnerable to zero-day attacks, facing significant blind spots in their defenses that malicious actors can exploit for their gain.
The Role of NDR in Zero-Day Threat Detection

Network Detection and Response (NDR) solutions have emerged as a critical component of modern cybersecurity strategies. Unlike traditional security measures that focus on perimeter defense or endpoint protection, NDR solutions operate at the network level, providing organizations with real-time visibility into their network traffic and identifying anomalous behavior indicative of a zero-day attack.
NDR solutions leverage advanced analytics, machine learning, and behavioral analysis techniques to detect deviations from normal network behavior that may signal the presence of a zero-day exploit.
By continuously monitoring network traffic and analyzing patterns and anomalies, Exeon.NDR, the Swiss-made NDR solution, can detect zero-day exploits as they emerge, enabling organizations to respond swiftly and effectively to mitigate potential damage.
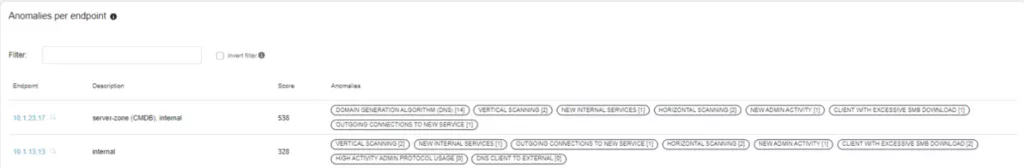
Furthermore, a platform like Exeon.NDR offers organizations the ability to conduct retrospective analysis, allowing them to investigate past network activity to identify indicators of compromise or suspicious behavior that may have gone unnoticed.
This proactive approach to threat detection and response enables organizations to stay ahead of emerging threats and minimize the impact of zero-day attacks on their systems and data.
In the subsequent sections, we will delve deeper into the capabilities of Exeon.NDR, exploring how it leverages advanced analytics and real-time monitoring to detect and mitigate zero-day exploits, and examine how it can enhance organizations’ overall cybersecurity posture.
Leveraging Advanced Analytics for Real-Time Detection
Exeon.NDR utilizes a sophisticated array of advanced analytics tools to bolster real-time threat detection capabilities, enabling organizations to preemptively identify and neutralize zero-day threats. Among these tools, machine learning algorithms do the heavy lifting, adept at parsing through immense volumes of network traffic to discern subtle anomalies that might signify the presence of an emerging zero-day exploit.
The Power of Machine Learning
These algorithms undergo training on historical data to establish a baseline of normal network behavior, allowing for the swift detection of deviations indicative of potential security breaches. Once the baseline is established, the tool continues to monitor historical behavior under a rolling time period, ensuring a constantly updated awareness of new potential threats.
By continuously monitoring network activity and cross-referencing data from diverse sources, Exeon.NDR can pinpoint zero-day exploits with remarkable accuracy, minimizing false positives and enabling organizations to uncover blind spots that may have previously been hidden.
Alongside machine learning, Exeon.NDR leverages complementary analysis methodologies such as behavioral analysis and anomaly detection. By scrutinizing network events, application interactions, and system activities, these techniques can flag irregularities that may signify an ongoing zero-day attack. This multifaceted approach not only enhances detection capabilities but also affords organizations a comprehensive understanding of their network environment.
Through the strategic application of advanced analytics for real-time threat detection, Exeon.NDR can provide organizations with the means to maintain a proactive stance against the evolving threat landscape. In the next section, we will examine exactly how Exeon.NDR could identify an emerging zero-day threat.
ML Applied: Ivanti Connect Secure VPN Exploited

In early 2024 Ivanti Connect Secure VPN faced severe security challenges due to multiple vulnerabilities (CVE-2023-46805 authentication bypass, CVE-2024-21887 command injection), and two additional vulnerabilities discovered later (CVE-2024-21888 privilege escalation, CVE-2024-21893 server side request forgery), one of which was a critical zero-day exploit. These vulnerabilities led to unauthorized access and data theft from a broad range of global organizations, including those in aerospace, banking, defense, government, and telecommunications.
Zero-day exploits such as these are commonly discovered in production environments around the world, leaving organizations with a limited response time to address these critical security breaches.
If an affected organization were to be using an NDR solution such as Exeon.NDR, it would have a chance to detect these unknown exploits by analyzing real-time network traffic and deviations from behavioral baselines. If we deconstruct the Ivanti Connect Secure VPN attack chain, we can examine how an NDR solution could identify and report this in real-time.
Ivanti Connect Secure VPN Exploitation Timeline:
1. Gaining Access
In the initial step, attackers exploited the CVE-2023-46805 vulnerability, allowing them to bypass authentication mechanisms on the VPN appliance. This action would be measurable, and seen as unexpected successful logins or access attempts from unusual IP addresses, possibly at atypical times, both of which have well defined baselines, allowing an NDR solution to potentially initialize an anomaly alert even at this early stage.
Next was the exploitation of CVE-2024-21887 – after gaining access, this exploit allowed the attackers to execute arbitrary commands on the appliance. This would generate unusual outbound connections from the VPN, and would trigger unexpected system changes. New outbound connections initiated by devices within the network to external servers is a closely monitored metric by NDR solutions, as this is often an initial step in an attack chain to maintain communication with the compromised systems via a command and control server.
2. Post-Access Behavior
Once the attackers had established access, their next step was to establish a foothold, using a Perl script to remount the filesystem. This Perl script was a sequence of commands that changed permissions or settings to allow previously restricted activities, such as executing files, or writing to areas that were previously protected, to be possible. This step facilitated the deployment of additional malware, and provided newly elevated privileges.
These steps could be caught by detecting new network traffic patterns as each step could possibly deviate from the established baselines.
An effective NDR solution may also flag atypical commands run with elevated privileges, such as the initial remounting of the filesystem, which is unlikely to be part of the regular administrative routines.
These new privileges enabled the deployment of Thinspool – a shell script dropper that allows malicious scripts to be delivered and executed on the target system, writing files in restricted directories or attempting to hide its activities.
Exeon’s baselining detections could determine if Thinspool initiated any services that are new or uncommon in the environment, especially any activity on an unusual port, or if it received connections from outside the network.
3. How Exeon.NDR Spots Threat Indicators
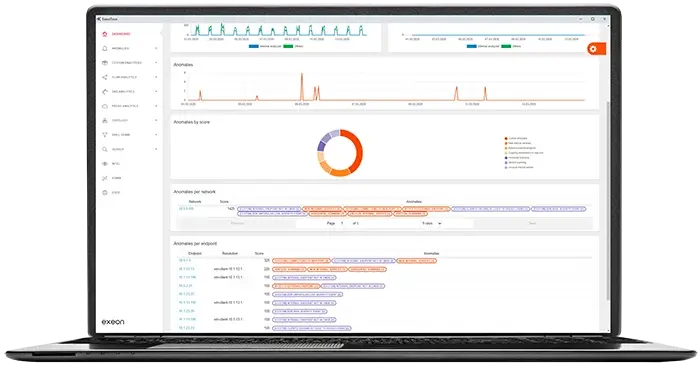
Thinspool acted as the initial dropper for the Lightwire/Wirefire web shells, scripts which are placed on a web server that enable further persistent access to the target system. Measurable network behavior metrics which may change at this step include increased HTTP(S) traffic, and communication with unusual endpoints to receive commands on.
Exeon’s analyzers would notice abnormal patterns in request volume, signaling potential web shell activity. Other analyzers also examine access requests through the proxy that do not follow typical authentication or usage patterns and could detect the attacker using a web shell to communicate with the compromised server. These proxy analyzers would detect anomalies in the volume and nature of proxy requests, additionally increasing the threat score and anomalies alerts triggered.
The next malware tool used was Warpwire, a JavaScript-based credential stealer, designed to capture plain text information such as usernames, passwords, emails, and more. This step allows for lateral movement within the network, and can potentially allow privilege escalation if valid credentials are found. Once credentials are captured, Warpwire would send them back to the control server via an HTTP GET request. This data exfiltration would create further unusual network traffic, with the outgoing data being sent to an unusual destination IP. Furthermore, the stolen credentials could lead to unusual internal network activity when unlikely systems are accessed using these credentials.
The final malware tool used was a passive backdoor known as Zipline, used to intercept network traffic. The malware receives encrypted commands and can remotely perform malicious activities without being easily detected. However, an increase of traffic to specific ports and services may be present, particularly an observable increase in encrypted traffic that does not follow the typical patterns of legitimate encrypted communication channels.
This example demonstrates the complexity and sophistication of the attacks leveraging the Ivanti vulnerabilities. The malicious actors utilized a mix of custom malware, script-based manipulations, and classic exploitation techniques like command injection and authentication bypass, much of which can go undetected without real-time traffic analysis. However, due to the broad network view and precise machine learning algorithms, even small deviations from baseline data can be detected by Exeon.
Individually, these might not raise alarms, but together, they form a pattern indicative of a security event happening in the network in real-time, eventually exceeding alerting thresholds and providing real-time insights into an ongoing security event. These rapid response capabilities are critical in the case of zero-day exploits, where every second counts in preventing data breaches or system compromise.

The latest “Perfect 10” CVSS:
Palo Alto Networks Firewalls Impacted by Zero-Day Vulnerability
Security analysts have recently discovered a critical zero-day vulnerability in Palo Alto Networks’ firewall systems. This vulnerability, identified as CVE-2024-3400, has been actively exploited since at least March 26, 2024.
The flaw, which scores a maximum of 10 on the Common Vulnerability Scoring System (CVSS), allows unauthenticated attackers to remotely execute arbitrary code with root privileges on affected systems. Palo Alto Networks has confirmed that this vulnerability impacts Pan-OS versions 10.2, 11.0, and 11.1. To exploit the flaw, the telemetry functions and either the GlobalProtect Gateway or GlobalProtect Portal (or both) must be operational on the firewall systems. Fortunately, Cloud Firewalls (NGFW), Panorama Appliances, Prisma Access, and older Pan-OS versions (9.0, 9.1, 10.0, and 10.1) remain unaffected.

In response to this critical issue, Palo Alto Networks has promptly released hotfixes for CVE-2024-3400 on April 15. These hotfixes are available for Pan-OS versions 10.2.9-h1, 11.0.4-h1, and 11.1.2-h3. Administrators are strongly advised to install these updates promptly or temporarily deactivate the telemetry feature until a comprehensive update can be implemented.
Strengthening Security Posture with Proactive Defense
In the relentless arms race against zero-day threats, NDR serves as an indispensable tool in fortifying an organization’s security posture. By integrating NDR capabilities into their cybersecurity arsenal, organizations gain a potent tool for preemptively identifying and preventing nascent threats before they can inflict harm.
By embracing a proactive defense posture supported by NDR, organizations can stay one step ahead of zero-day exploits and safeguard their critical assets from exploitation.
In conclusion, the evolving landscape of cybersecurity, marked by the persistent threat of zero-day attacks, demands a proactive and multifaceted approach to defense. Traditional security measures, while valuable, exhibit inherent limitations in combating the dynamic nature of zero-day threats, necessitating the integration of NDR solutions such as Exeon.NDR.
By leveraging advanced real-time analytics, diverse data sources, and retrospective analysis capabilities, NDR solutions empower organizations to detect, mitigate, and preemptively respond to zero-day exploits in an unprecedented way.
Yet, as the cyber threat landscape continues to evolve, with adversaries employing increasingly sophisticated tactics, the future of cybersecurity remains uncertain. How will emerging technologies, regulatory frameworks, and collaborative efforts shape the next phase of cyber defense? We’ll keep you updated.